the spine collector vulture
The spine collector vulture, also known as the Egyptian vulture, is a fascinating and unique bird of prey that has captured the attention of scientists and bird enthusiasts alike. With its striking appearance and unusual feeding habits, the spine collector vulture has become a symbol of conservation efforts and the importance of preserving biodiversity in our ecosystem.
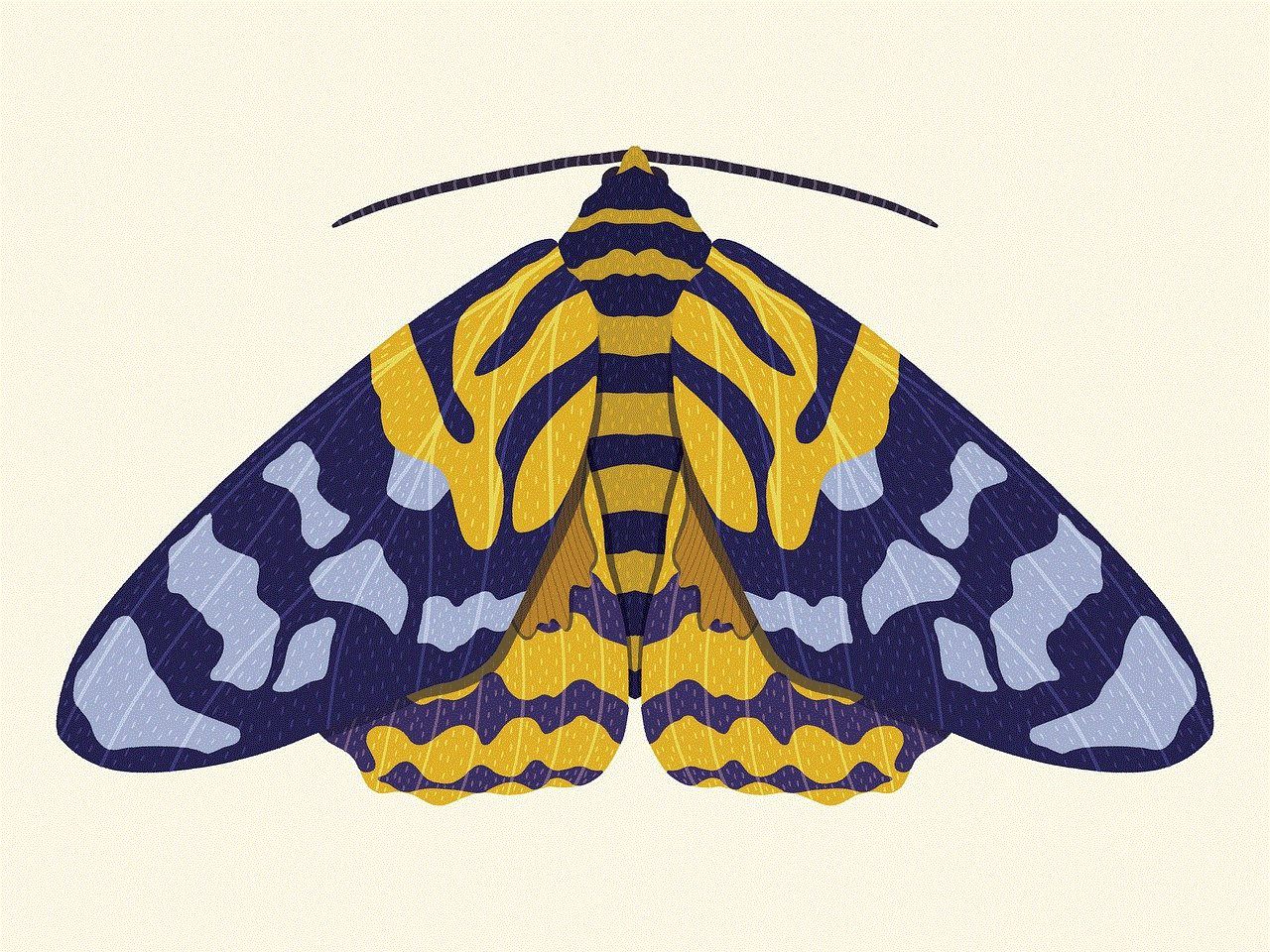
The spine collector vulture, or Neophron percnopterus, is a medium-sized bird that can reach a wingspan of up to six feet. It is easily identifiable by its white and black plumage, with a distinctive yellow face and beak. This bird is found in parts of Europe, Africa, and Asia, and is known for its scavenging behavior and ability to adapt to various environments.
One of the most intriguing aspects of the spine collector vulture is its feeding habits. Unlike other vultures that primarily feed on carrion, the spine collector vulture has a more diverse diet. While it does scavenge for carcasses, it also feeds on insects, eggs, and even small mammals. This unique diet has earned it the nickname of “bone breaker” or “spine collector” due to its ability to break open bones and eat the nutritious marrow inside.
The spine collector vulture is also known for its clever hunting techniques. It has been observed dropping hard-shelled objects, such as bones or rocks, from a height onto the ground to break them open and access the tasty treats inside. This behavior is not only impressive but also essential for the survival of the species. With the decline of large carcasses due to human activities, the spine collector vulture has had to adapt to a more diverse diet to ensure its survival.
Another interesting aspect of the spine collector vulture is its unique nesting behavior. Unlike other vultures that build nests in trees or on the ground, the spine collector vulture prefers to nest on cliffs. This provides protection for their young from predators, as well as access to open areas for catching prey. The nesting sites are usually located near a reliable food source, making it easier for the parents to feed their young.
Unfortunately, the spine collector vulture is facing numerous threats to its survival. The main threat comes from humans, as their habitats are being destroyed and their food sources are dwindling. Poisoning is also a significant issue, as the vultures can ingest toxic substances when feeding on contaminated carcasses. As a result, the population of spine collector vultures has declined significantly in recent years, and the species is now listed as endangered on the IUCN Red List.
Conservation efforts have been put in place to help protect the spine collector vulture and ensure its survival. One such effort is the implementation of vulture safe zones, where farmers are encouraged to dispose of livestock carcasses in designated areas away from the vultures’ habitats. This reduces the risk of poisoning and ensures a steady food supply for the birds.
Another crucial conservation effort is the establishment of breeding programs in captivity. These programs aim to increase the number of spine collector vultures through breeding and release of the birds into the wild. This has been successful in some areas, and the released birds have been observed breeding in the wild, which is a positive sign for the species’ future.
In addition to these conservation efforts, education and awareness campaigns are also crucial in preserving the spine collector vulture. By educating people about the importance of these birds in our ecosystem, we can reduce the negative impact of human activities on their populations. This includes raising awareness about the dangers of using pesticides and poisoning carcasses, as well as promoting sustainable farming practices.
The spine collector vulture is not only important as a species but also plays a vital role in our ecosystem. As scavengers, they clean up carcasses, preventing the spread of diseases and keeping the environment clean. They also help control pest populations, such as insects and small mammals, which can have a significant impact on agriculture and human health.
In conclusion, the spine collector vulture is a remarkable bird that has captured our fascination and admiration. Its unique appearance, feeding habits, and nesting behavior make it a vital and valuable species in our ecosystem. However, due to human activities, the spine collector vulture is facing severe threats to its survival. It is our responsibility to take action and ensure the conservation of this beautiful and essential bird for future generations. By working together, we can protect the spine collector vulture and all wildlife and preserve the delicate balance of our natural world.
advanced security products
Title: Advanced Security Products: Defending the Digital Frontier
Introduction:
In an increasingly interconnected world, the need for robust security measures has become paramount. From personal data breaches to sophisticated cyber-attacks on critical infrastructure, organizations and individuals alike are facing an ever-evolving threat landscape. To counter these threats, advanced security products have emerged as a vital line of defense. This article explores the various facets of advanced security products, their importance, and their role in safeguarding our digital lives.
1. Understanding Advanced Security Products:
Advanced security products encompass a wide range of technologies and solutions designed to protect against cyber threats. These products go beyond traditional antivirus software and firewalls, providing comprehensive protection against emerging threats. They include advanced threat detection systems, encryption tools, biometric authentication, intrusion detection systems, and more.
2. The Importance of Advanced Security Products:
As cybercriminals become more sophisticated, organizations must adopt advanced security products to stay one step ahead. Cyber threats can disrupt operations, compromise sensitive data, and lead to financial and reputational damages. Advanced security products ensure organizations are equipped to defend against these threats by proactively identifying vulnerabilities, detecting and mitigating attacks, and protecting essential data assets.
3. Advanced Threat Detection Systems:
Advanced threat detection systems are at the forefront of modern security products. Utilizing artificial intelligence (AI) and machine learning (ML), these systems analyze vast amounts of data to identify patterns, anomalies, and potential threats. They can detect complex malware, zero-day attacks, and even insider threats, providing real-time alerts and actionable insights to security teams.
4. Encryption Tools:
Encryption is a critical component of modern security products. It ensures that data in transit or at rest remains secure from unauthorized access. Advanced encryption tools employ robust algorithms and cryptographic protocols to protect sensitive information, making it virtually impossible for attackers to decipher or manipulate.
5. Biometric Authentication:
Traditional password-based authentication methods are increasingly vulnerable to hacking attempts. Advanced security products employ biometric authentication, leveraging unique physiological and behavioral characteristics such as fingerprints, facial recognition, or voice recognition. Biometric authentication adds an extra layer of security, making it more challenging for unauthorized individuals to gain access.
6. Intrusion Detection Systems:
Intrusion Detection Systems (IDS) are crucial for organizations to detect and respond to network intrusions. These systems monitor network traffic, identifying suspicious activities and potential attacks. Advanced IDS utilize machine learning techniques to identify known attack patterns and adapt to new threats in real-time, enhancing the organization’s ability to respond swiftly and effectively.
7. Security Information and Event Management (SIEM):
SIEM solutions are another integral component of advanced security products. SIEM platforms aggregate and correlate security event information from various sources, providing a centralized view of an organization’s security posture. By analyzing logs, identifying patterns, and applying threat intelligence, SIEM tools help organizations detect and respond to security incidents promptly.


8. Proactive Threat Intelligence:
Advanced security products leverage proactive threat intelligence to anticipate and mitigate potential threats. By constantly monitoring the threat landscape, these products provide real-time information on emerging vulnerabilities, malware, and attack vectors. This enables organizations to proactively update their security measures, patch vulnerabilities, and stay ahead of cybercriminals.
9. Securing the Internet of Things (IoT):
The proliferation of IoT devices brings new security challenges. Advanced security products address these challenges by providing robust IoT security solutions. This includes securing devices, network communication, and data exchange, ensuring that IoT deployments are not compromised and do not become entry points for cybercriminals.
10. The Future of Advanced Security Products:
As the threat landscape continues to evolve, advanced security products must adapt and innovate. The integration of AI, ML, and automation will play a crucial role in enhancing security capabilities. Additionally, the rise of quantum computing poses both opportunities and challenges for advanced security products, necessitating the development of quantum-resistant encryption algorithms.
Conclusion:
Advanced security products have become indispensable in today’s digital world. The continuously evolving threat landscape demands proactive, intelligent, and comprehensive security solutions. From advanced threat detection systems to encryption tools and proactive threat intelligence, these products provide the necessary defenses to safeguard against cyber threats. As technology advances, it is imperative for organizations and individuals to stay vigilant, adopting and implementing advanced security products to protect their digital assets and maintain trust in the digital frontier.
are send its anonymus
Are Send Its Anonymous: The Rise of Anonymous Messaging Apps
In today’s digital age, where privacy and anonymity have become increasingly important, anonymous messaging apps have gained immense popularity. These apps allow users to communicate with each other while keeping their identities secret. One such app that has gained significant attention is “Are Send Its Anonymous.” In this article, we will explore the rise of anonymous messaging apps, the benefits they offer, the concerns they raise, and their impact on society.
Anonymous messaging apps have been around for quite some time, but their usage has skyrocketed in recent years. The need for privacy and the desire to express oneself without fear of judgment or consequences have been the driving factors behind this surge. Are Send Its Anonymous, like other anonymous messaging apps, allows users to send messages and engage in conversations without revealing their true identities. This anonymous feature has made it extremely popular among teenagers and young adults who are looking for a safe space to share their thoughts and feelings.
One of the primary benefits of anonymous messaging apps like Are Send Its Anonymous is the freedom it provides. Users can express themselves without fear of judgment or backlash. This anonymity fosters honest and open conversations that may not be possible in real life. People can discuss sensitive topics, seek advice, or simply vent without the fear of repercussions. This can be particularly helpful for individuals dealing with mental health issues who may find solace in sharing their experiences anonymously.
Another advantage of anonymous messaging apps is the ability to connect with like-minded individuals. Are Send Its Anonymous allows users to join various interest-based groups or communities, where they can interact with people who share similar interests or experiences. This sense of community can be empowering and comforting, especially for those who may feel isolated or misunderstood in their real-life social circles. Through these apps, users can find support, guidance, and companionship from individuals who can relate to their struggles or interests.
However, the rise of anonymous messaging apps also raises concerns regarding misuse and abuse. The cloak of anonymity can embolden individuals to engage in cyberbullying, harassment, or spreading false information. This can lead to severe consequences for the victims and can have a detrimental impact on mental health. Are Send Its Anonymous, like other similar apps, has implemented measures to combat such issues, including reporting and blocking features. However, it’s crucial for users to exercise caution and responsibility while using these apps to ensure a safe and positive experience for everyone involved.
Furthermore, the anonymity provided by these messaging apps can also be exploited by individuals with malicious intent. Criminal activities, such as cyberstalking, grooming, or even planning illegal activities, can take place behind the veil of anonymity. Law enforcement agencies have faced challenges in investigating and preventing such offenses due to the difficulties in identifying the perpetrators. This highlights the need for a delicate balance between privacy and security in the digital world.



The impact of anonymous messaging apps on society is multifaceted. On one hand, they offer a platform for free expression and open communication. They provide a space for marginalized communities to voice their opinions and experiences without fear of judgment or discrimination. This can lead to increased awareness and empathy towards various social issues. On the other hand, the misuse of these apps can contribute to the spread of hate speech, misinformation, and online toxicity. It is essential for app developers, users, and society as a whole to address these challenges and work towards creating a safer and more inclusive digital environment.
In conclusion, the rise of anonymous messaging apps like Are Send Its Anonymous reflects the growing need for privacy and anonymity in our digital society. These apps offer a safe space for individuals to express themselves, connect with like-minded people, and seek support. However, they also raise concerns regarding misuse, abuse, and potential criminal activities. Striking a balance between privacy and security is crucial in ensuring a positive and responsible use of anonymous messaging apps. As technology continues to evolve, it is essential to adapt and develop mechanisms to address these challenges and shape a digital landscape that respects both privacy and accountability.
